CSAW
Perfect Secrecy
Challenge Description:
Alice sent over a couple of images with sensitive information to Bob, encrypted with a pre-shared key. It is the most secure encryption scheme, theoretically…
image1:
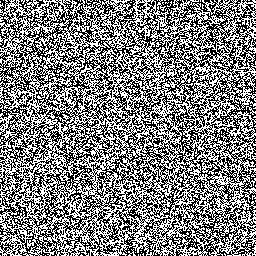
image2:
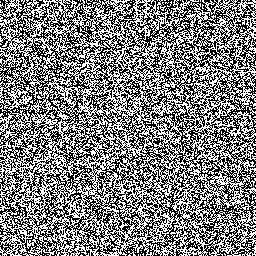
The two images I’m given, remind me of a topic I learned in Serious Cryptography where the Linux penguin was encrypted using ECB. I know that ECB was not used to encrypt this image because the image is not still visible as the Linux penguin was.

The challenge description says that it was encrypted using the most secure encryption scheme, which is AES. To decrypt AES, I need the secret key. Not entirely sure as to how I’m going to find that. The way I’d solve this would be to translate the given images into text, then using an AES decryptor online to decrypt the images, and then translating them back into images. This is assuming I have the secret key.
After discussing the problem with others, I realized that the most theoretically secure encryption scheme is a one time pad. Now I just need the key, which I now know is as long as the plaintext itself. Still not sure how to get the key, though.
Update
So since the most theoretically secure encryption scheme is the one time pad, I don’t need to know the key beforehand since the key was probably used to encrypt both images. The way the one time pad works is by xor-ing the message with the key, but if the same key was used for both messages, I can xor the messages together and leak the key.
The python script below xors the two images together using the PIL library and returns the new image (key):
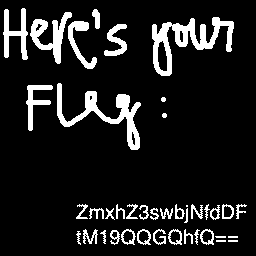
difib
Challenge Description:
Welcome to crypto. We start with the classics! Deliver the decrypted form of the message to the guard on your journey.
message:
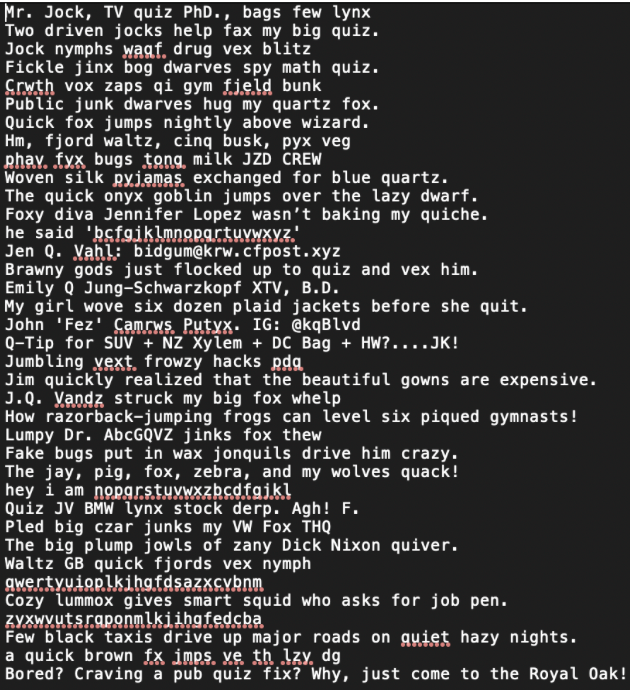
ramblings:
hints:
Update
The challenge’s title tells us that this is a bifid cipher. According to Wikipedia, “the bifid cipher is a cipher which combines the Polybius square with transposition, and uses fractionation to achieve diffusion”.
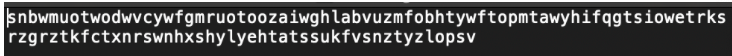
Connecting to the server using the netcat command gives us this ciphertext to decrypt: snbwmuotwodwvcywfgmruotoozaiwghlabvuzmfobhtywftopmtawyhifqgtsiowetrksrzgrztkfctxnrswnhxshylyehtatssukfvsnztyzlopsv
To use a bifid cipher, we need to have a key that is a perfect panagram (sentence that uses each letter of the alphabet once) of 25 characters. In the encrypted message, ‘j’, is not used, so we need to take out every ‘j’ that appears in ramblings.txt, and every character that is non-alphabetic.
CTF Writeup: [Kooli CSAW Crypto] (https://a-kooli.me/post/csaw-ctf-2020-quals-crypto/#difib)
modus operandi
Challenge Description: Can’t play CSAW without your favorite block cipher!
When I run the netcat command, I’m asked to input a plaintext, the corresponding ciphertext is outputted. I’m then prompted to determine whether ECB or CBC mode was used to encrypt the plaintext. ECB and CBC mode are used with AES encryption. So I’m assuming the cipher used is AES.
The hint given for this challenge is: “<200”. This could represent the key size or the block size.
Assuming that the cipher is using one mode of operation consistently with each prompt, I’m thinking the best way to solve this is to continually input plaintext and keep track of the ciphertext returned. I think this would potentially be the best way to solve it because ECB is known as an inferior mode of operation because of its lack of diffusion (i.e. the Linux penguin encryption example).
